How IT Became The Great Equalizer
The astonishing advancements in Information Technology over the past few decades have done wonders for business processes and efficiency. In many ways, it has leveled the playing field, giving smaller organizations the capacity and resources to perform on the level of many of their bigger competitors, giving them tools that were once out of reach because the high-cost of implementing IT infrastructure.
As costs came down, IT-related product offerings went up and potential markets expanded. As a result, full utilization of advanced technologies that were once considered luxuries reserved for the most advanced organizations, became a necessity for many businesses because the lowered cost-of-entry simply made it unwise for most businesses to not adapt IT infrastructures.
Dependency Can Increase Vulnerability
Just as these advancements made businesses more efficient in terms of process, it has made them dependent on their IT infrastructures, as many applications and information stored on these business networks have become mission-critical.
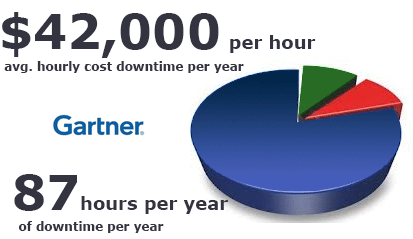
Downtime is an inevitable reality of IT. Every single piece of hardware and software on the market, from the personal to enterprise level, is susceptible to downtime in one form or another whether it be in the form of a brief system outage, misconfiguration, or all out system failure. It is a topic that is terrifying to many businesses and IT consulting professionals, and one that many people would rather not address and hope it doesn’t apply to them.
“The average cost of these outages to SMBs is around $12,500 per day of outage.”
The reluctance to talk about these issues not only proves detrimental to many businesses financial and legal status, but it also makes IT consultants money – A LOT of money. A paper recently published by the Ricoh Corporation tells us that the median number of system outages experienced by the average small or medium business each year is six. The average cost of these outages to Small Medium-Sized Businesses (SMBs) is around $12,500 per day of outage.
Pay Now or Pay More Later
The fact of the matter is, it is much more cost-effective for businesses and organizations to take a proactive approach to managing and monitoring their system’s health, than it is to employ a break-fix method of system maintenance. Not only are the direct IT costs much less with proactive maintenance, but the potential losses due to reputation damage, revenue loss, legal implications, and other process malfunctions are virtually mitigated or eliminated.
The biggest threats to SMB systems as listed by the report are terrorism, natural disasters, criminal activity, data loss, and cyber-attacks. Data loss and cyber-attacks are heavily atop that list. The top areas where most SMBs currently need improvement as identified by the report are computer security, backup-recovery + archiving, and disaster preparedness. Other areas identified for improvement are computing performance, data storage capacity, and computing costs.
Implementing a plan that includes a comprehensive proactive approach with managed IT services, such as those offered by CATS Technology Solutions Group, will dramatically decrease the chances of an outage occurring, and provide the following benefits to your business:
Increased Employee Efficiency
Since employees workstation and network access issues are minimized, employees are free to perform their jobs, and don’t have to worry about being incapacitated by the IT infrastructure, or becoming a pseudo-technician by employing faulty, temporary end-user fixes that could actually compromise your network further, causing a more troublesome issue down the road.
Enhanced Network Performance
With a proactive monitoring and maintenance plan in place, software patches, hotfixes, antivirus updates, security activities, and other system maintenance is performed on a regular schedule, in the background of regular use, which means your employees activities are not affected by these functions.
Better Assurance For Business Continuity
Your environment is consistently monitored and many events are prevented. When they do happen however, they are immediately identified and resolved, before the effects have an impact on day-to-day operations.
If your business can easily withstand the financial, legal, and reputation damages associated with complete loss of all data, loss of use of every computerized system used in operations, an unauthorized outside party gaining full-access to confidential business information, and devastating damage to the entire hardware infrastructure of its environment, then proactive managed IT services for business wouldn’t be a wise investment.
If on the other hand, your company is one that values efficiency, privacy, and productivity, retaining and IT consulting service is not only wise, but virtually necessary.
Just as every IT environment is unique in form and function, so should the approach to proactive maintenance and security be.
To see where you would stand in the event of an IT catastrophe, contact CATS Technology Solutions Group today for a complete no-cost and no-obligation analysis of your IT environment.



