Understanding the Dark web
The dark web is only a fraction of the much larger “deep web”, which can be defined as a part of the web that cannot be accessed normally. The deep web is a part of the internet not indexed by search engines, meaning you need special software and to essentially know what you’re doing to access it.
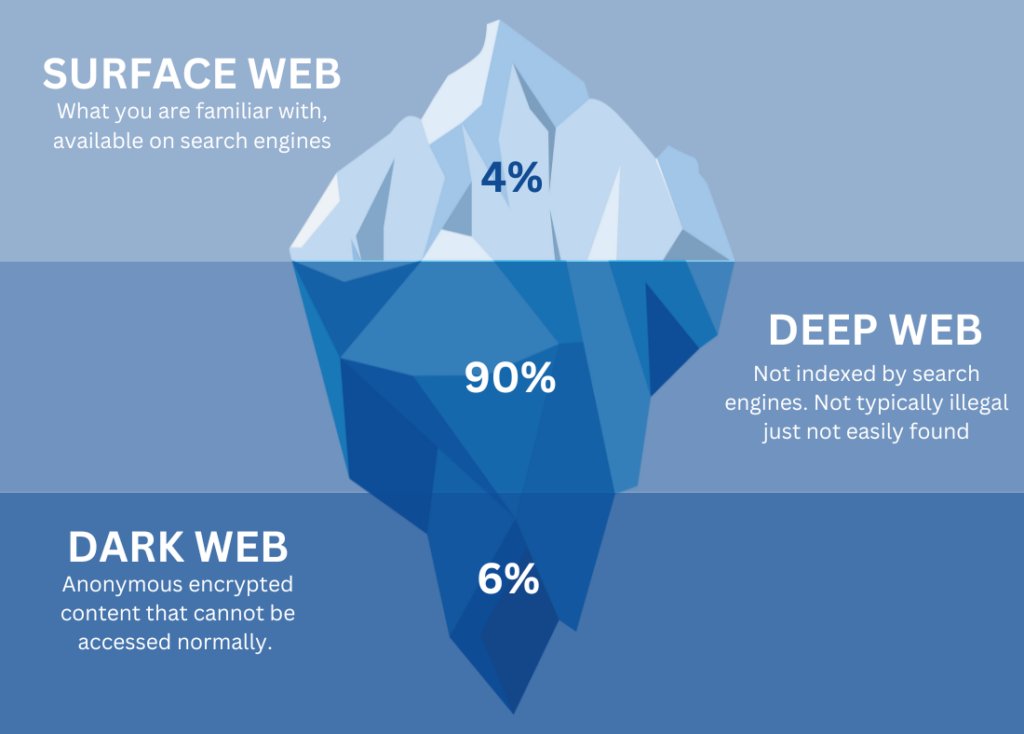
The Dark web accurately reflects its name, its untraceable nature acts as a shield for any who hide beneath its surface. This makes it the perfect resource for criminals, specifically ones committing cybercrimes.
Lifecycle of a cybercrime
If you or your business have fallen victim to a cyber-attack, it is likely your data found its way onto the dark web. And while we have previously discussed the many techniques cyber criminals use to steal data we have not quite gone into what happens with what they have stolen.
- Sold in secret auctions to the highest bidder.
- Bundled with other stolen data for sale.
- Used in blackmail or extortion schemes.
- Traded for services or expertise from other cybercriminals.
- Used in identity theft, fraud, or financial crimes.
- Exchanged for cryptocurrency or digital assets.
what else lurks in the dark?
Stolen data isn’t the only thing cybercriminals share on the dark web. They also share tools and resources that help them carry out their operations.
- Hacking tools and Exploit Kits: Automated tools for hacking.
- Security bypass methods: Strategies for bypassing security measures.
- Malware development and distribution: Creation and sale of malicious software.
- Forums and communities: Platforms for sharing knowledge and tactics.
- Threat intelligence: Trading information about potential targets.
Flip the script
Defending against cyber threats, especially those from the dark web, is crucial. It’s vital to be proactive with your cyber security. CATS Technology stands ready to fortify your defenses and support you by implementing measures such as:
- Establishing baseline cyber security practices
- Employee cyber security training
- Dark web monitoring services
- Advising on best practices for password management
- Data encryption
- Cyber security and network monitoring
- Vendor verification processes
Get in touch today to learn more about implementing measures of security and dark web monitoring.




